If you have the ability to SSH into a remote machine you also have the ability to direct your web browser’s traffic through SSH to that machine. This can be quite handy for browsing the (remote) local network without opening a HTTP port on the firewall.
First, install Putty and Firefox. Putty can be found here and Firefox here. If you’re not sure which file to download for Putty, just go for putty.exe. Once you’ve downloaded Putty, open it and you should see a screen like this:
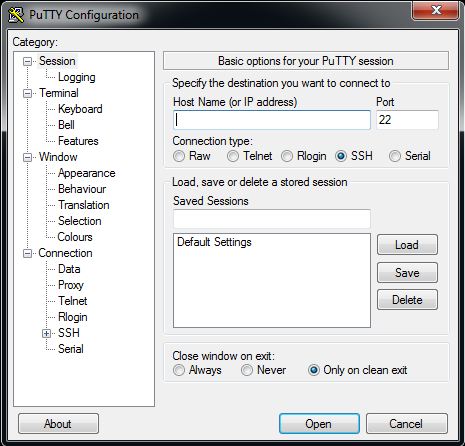
Enter in the remote computer’s IP address and SSH port number (usually 22 unless you changed it) and test the connection to make sure you can log in. If that works, disconnect and go to Connection -> SSH -> Tunnels like so:
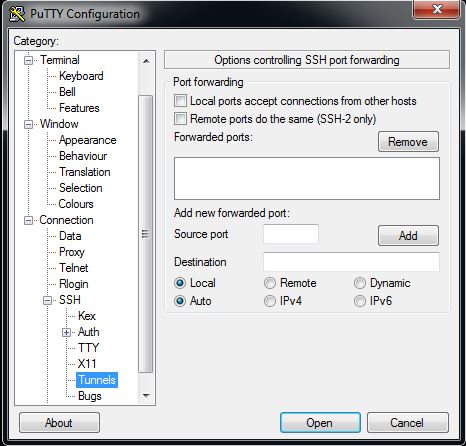
then change the selection from Local to Dynamic. After that, enter 2048 into the “Source port” field and click Add. Your screen should now look like:
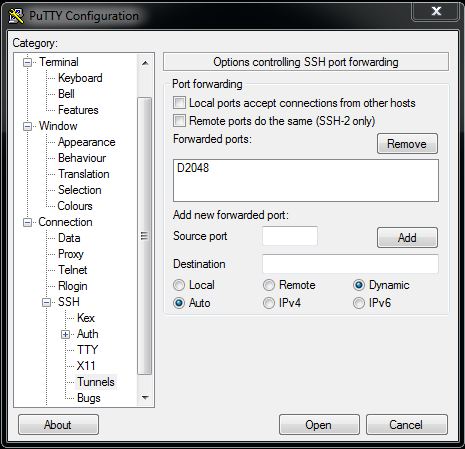
Note the D in front of the source port number – that should be there.
Scroll back up on the left until you get back to the original Session window. Check the IP address and port numbers and enter a name in the “Saved Sessions” box, then click Save. Now you can load these settings again next time you open Putty.
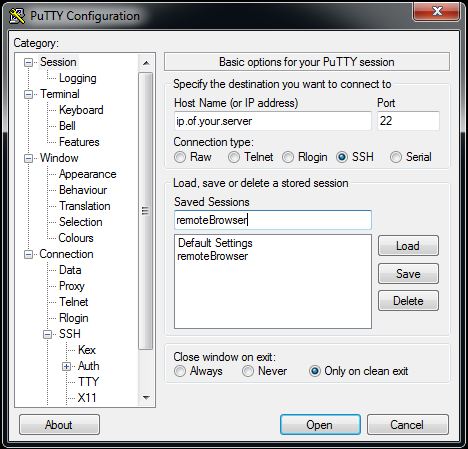
The version of Firefox we’re using for today’s example is 18.0.2. Go to Tools -> Options -> Advanced (you may have to hit Alt to bring up the Tools menu at the top):
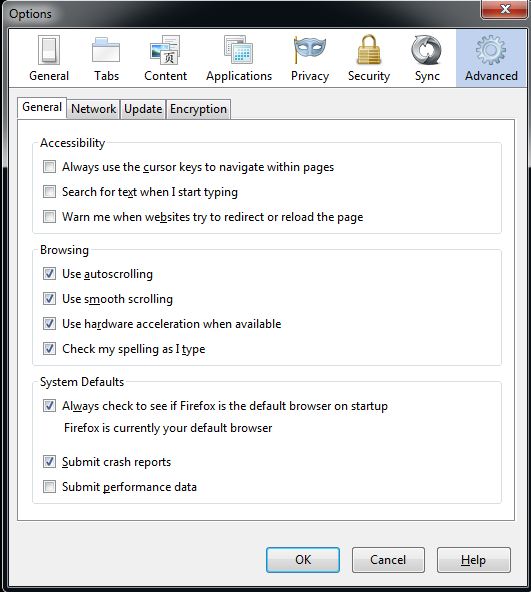
Now choose Network then Settings. You should see a window like this:

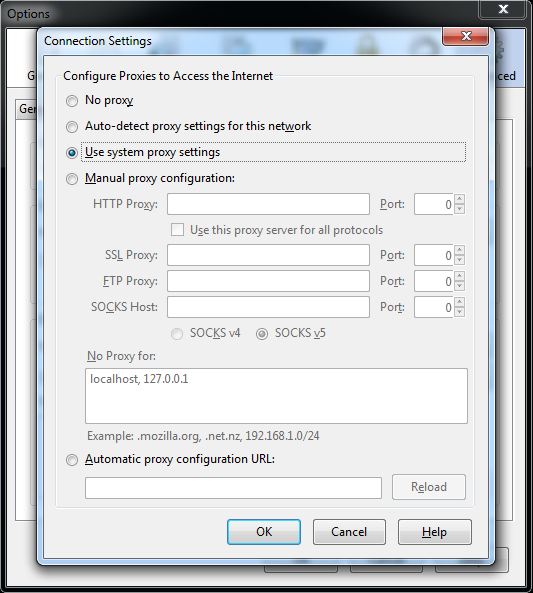
Now choose “Manual proxy configuration” and enter localhost in SOCKS Host, and 2048 in the corresponding Port field like so:
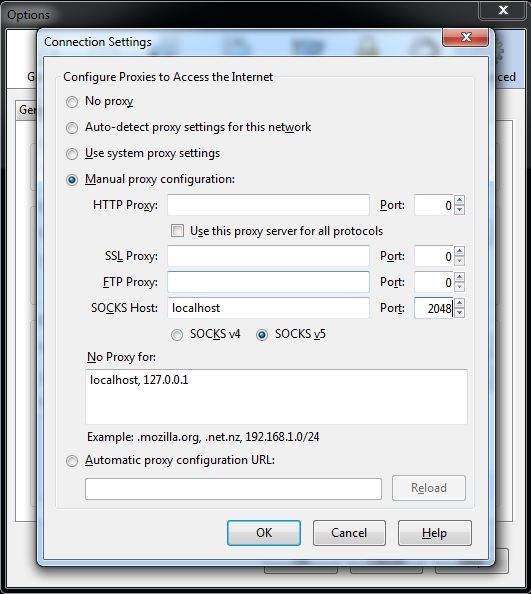
Click OK then again on the previous screen, open your Putty connection and the next URL you enter should be tunneled through to your remote server! To undo this, simply go into Firefox and put the above screen back to “Use system proxy settings”.